#Greedy Algorithm implementation C
Explore tagged Tumblr posts
Video
youtube
LEETCODE 135 : L2R2L SUM PATTERN: CANDY : C++ SOLUTION
LeetCode Problem 135, "Candy," is a greedy algorithm problem where each child in a row must receive candy, adhering to the following rules: every child must have at least one candy, and children with a higher rating than their immediate neighbors must receive more candy than those neighbors. The goal is to distribute the minimum number of candies while satisfying these conditions. The problem is typically solved by making two passes through the list of ratings: one from left to right and another from right to left, adjusting the candy count based on the children's relative ratings. The challenge tests one's ability to implement efficient greedy strategies.
0 notes
Text
Crack the Code: Acing the Coding Aptitude Test
In the rapidly evolving landscape of technology and software development, coding aptitude tests have become a cornerstone of the hiring process for many tech companies. These tests assess a candidate's coding skills, problem-solving abilities, and logical thinking – all crucial traits for success in the world of programming. This blog delves into the intricacies of hiring using coding aptitude tests, offering a comprehensive guide to help aspiring developers and tech enthusiasts excel in this critical aspect of job interviews.

Understanding Coding Aptitude Tests:
Coding aptitude tests are designed to evaluate a candidate's ability to write clean, efficient, and logical code to solve programming problems. These tests come in various formats, ranging from multiple-choice questions to hands-on coding challenges, and are tailored to assess a candidate's knowledge of programming languages, algorithms, data structures, and problem-solving methodologies.
Key Components of Coding Aptitude Tests:
a) Algorithmic Problem Solving: Candidates are presented with algorithmic challenges that require creative thinking to design efficient solutions. Employers are interested in a candidate's ability to optimize code for performance.
b) Data Structures: Tests often include questions about various data structures such as arrays, linked lists, trees, and graphs. Candidates need to choose the appropriate data structure to solve a given problem.
c) Coding Syntax and Logic: Candidates are assessed on their ability to write code that adheres to the syntax of a specific programming language while effectively implementing the required logic.
d) Time and Space Complexity: Candidates are expected to analyze the time and space complexity of their solutions, demonstrating an understanding of efficient code execution and memory usage.
Preparing for Coding Aptitude Tests:
a) Strengthen Core Concepts: Build a strong foundation in programming languages, data structures, and algorithms.
b) Practice Regularly: Solve a variety of coding challenges on platforms like LeetCode, HackerRank, and Codeforces to enhance problem-solving skills.
c) Understand Patterns: Recognize common patterns and techniques used in coding problems, such as dynamic programming, recursion, and greedy algorithms.
d) Time Management: Practice solving problems under time constraints to improve speed and efficiency during the test.
Approaches During the Test:
a) Read Carefully: Carefully read the problem statement, input/output specifications, and constraints before diving into coding.
b) Plan First: Spend time planning and outlining your approach before starting to code. A well-thought-out plan can lead to cleaner code.
c) Test Thoroughly: Test your code with different test cases to ensure its correctness. Debugging skills are as important as writing the code itself.
d) Optimize as Needed: Once you have a working solution, consider optimizing it for better time and space complexity if possible.
Tips for Success:
a) Practice Consistently: Consistent practice is key to improving your coding skills and problem-solving abilities.
b) Learn from Mistakes: Don't be discouraged by failures. Analyze your mistakes and learn from them to improve in the future.
c) Stay Updated: Keep up with the latest trends in programming and coding techniques to stay competitive in the job market.
d) Stay Calm: During the test, stay calm and focused. Time pressure can lead to mistakes, so maintain a clear mind.
youtube
Conclusion:
Acing the coding aptitude test is not only about demonstrating technical prowess but also about showcasing your ability to approach complex problems with creativity and logic. By understanding the components of coding aptitude tests, preparing diligently, practicing consistently, and adopting effective problem-solving strategies, you can confidently tackle coding challenges during interviews and set yourself on the path to a successful career in software development. Remember, cracking the code isn't just about solving problems – it's about demonstrating your potential to become an exceptional coder.
SITES WE SUPPORT
Aptitude Assessment – Weebly
1 note
·
View note
Text
C# - Coin change problem : Greedy algorithm
C# – Coin change problem : Greedy algorithm
In this article, we will discuss an optimal solution to solve Coin change problem using Greedy algorithm.
A greedy algorithm is the one that always chooses the best solution at the time, with no regard for how that choice will affect future choices.Here, we will discuss how to use Greedy algorithm to making coin changes. It has been proven that an optimal solution for coin changing can always…
View On WordPress
#Coin change C#Coin change problem C#Coin change using Greedy algorithm#Greedy Algorithm C#Greedy Algorithm implementation C
0 notes
Text
ktre
A regular expression engine in pure C (3339 lines, 2755 sloc).

I call this engine ktre, which means “Krok’s Tiny Regex Engine.” It implements a backtracking implementation of PCRE-flavored regular expressions in a single header for easy embedding. A short feature list:
• Submatching • Backreferencing • Named capture groups • Subroutine calls • Recursion • Positive and negative lookahead assertions • Arbitrary positive and negative lookbehind assertions
The basic algorithm for the execution of the generated bytecode is based on “threads” of execution. When a conditional metacharacter (like `?`) is executed, the VM splits execution into two paths, one path of execution attempts to find a match that includes the character being matched conditionally, and the other path attempting to find a match that does not include the character being matched conditionally. In fact, all of the basic quantifiers are implemented by different permutations of branching instructions interwoven with the actual text to match. The instruction that implements this “splitting” behavior is called INSTR_BRANCH, if you’re following along with the code.
Here’s what the pre-runtime debugging info for `foo?` looks like:
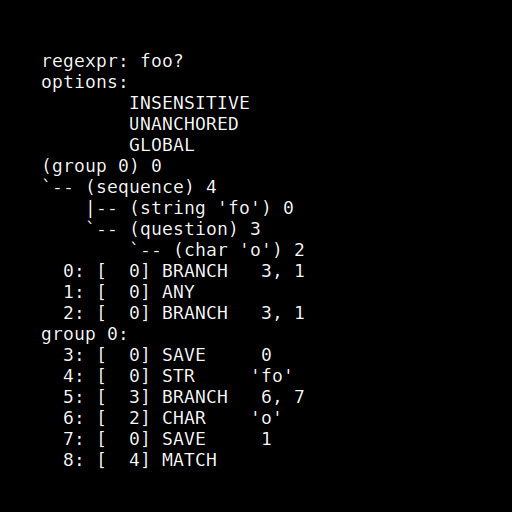
In this image, “regexpr:” indicated the expression being compiled. It’s followed by a list of the options passed to the engine for this particular compile. The next item is an abstract syntax tree (AST) representing the expression. The last item is the bytecode that the AST was compiled into. `group 0:` indicates that the location it marks is the beginning of the 0th group (the entire match). When a text editor or general purpose language like Perl supports regular expressions in the syntax the flags are often passed as single-character flags as some part of the string-like syntax required. For example, the expression we’re looking at now would be written in Perl like `/foo?/gi`. The `g` passes the global option to the engine, and `i` passes the insensitive option.
You might notice some odd things about the bytecode. The first three instructions are outside of the 0th group, so it will not be part of the match. Why are we matching stuff that’s not in the expression? These first three instructions implement the unanchored matching passed to the engine as a flag. If you following the execution with your mind you may realize what’s happening. The first instruction has us attempt to match the regex at the first position in the subject string. If that fails, we’ll fall back to the 1st instruction, which consumes a single character and then tries to match the regex again. If that fails, it consumes another character &c. The behavior of these instructions is identical to the behavior of `.*?` - a so-called “non-greedy” quantifier.
This simple example demonstrates how backtracking works. Here’s what the execution looks like:

Because ktre uses backtracking to find matches, it is essentially an implementation of a kind of nondeterministic finite automaton (NFA). This means that in a worst case scenario it may take exponential time to complete its execution.
An interesting ktre feature is arbitrary (variable-width) lookbehind assertions; most engines support only lookbehind assertions that match text of one length.
Unfortunately, ktre does not support Unicode. Basic Unicode strings will work as intended, but applying a quantifier like `?` to a multi-byte Unicode character can cause erroneous matches with seemingly unrelated character because the engine is not aware of code-points - it works only on individual bytes.
0 notes
Text
Solving the 8 puzzle problem using A* (star) algorithm
In this tutorial, we will solve the 8 puzzle problem using A* (star) search or pathfinding algorithm. Besides, the primary algorithm (A*), we will also use breadth-first, depth-first and greedy best-first search algorithms to find a solution for the 8 puzzle problem. We will approach the solution by first modelling the problem, then by building the fundamental blocks and finally applying a solver to solve the puzzle. Read Also: How to Generate Mazes Using Depth-First Algorithm This tutorial will provide the solution both from the algorithmic perspective as well as by providing the implementation of the algorithms using C++ for a console program and C# for Unity scripting. Finally, we will implement an 8 puzzle game using Unity and solve a random state of the puzzle by applying the A* algorithm. Click to Play the Unity Game
Introduction
Typically A* (Astar) is used in a grid-based pathfinding problem. However, as a general rule, any pathfinding algorithm (A* included) can be used to solve any graph-based problem. For a very detailed understanding of path-finding, I suggest the brilliant tutorial maintained by Amit in his Stanford’s site. In this tutorial I am not going to go through the theory of A* pathfinding, but rather, I would implement all necessary functions for A* pathfinding to solve the 8 puzzle problem.
The 8 Puzzle Problem
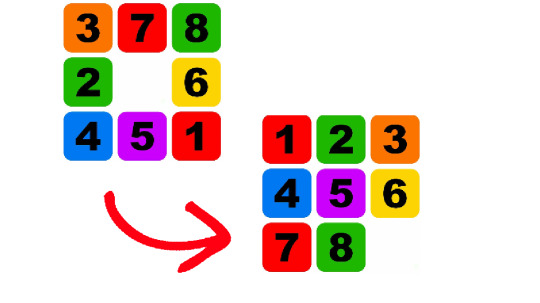
The 8-puzzle problem is a puzzle that was invented and popularized by Noyes Palmer Chapman in the 1870s. The 8-puzzle is a smaller version of the slightly better-known 15-puzzle. It comprises a 3-by-3 grid with 8 square blocks labelled 1 through 8 and a blank square. The goal is to rearrange the blocks so that they are in order with the blank sometimes at the start or at the end. The diagram above shows one possible initial configuration and the goal. To reach the goal state you are permitted to slide blocks horizontally or vertically into the blank square.
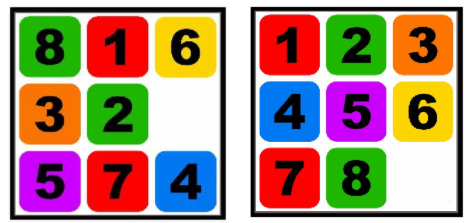
Before we can solve the puzzle we will need to model the problem. But what is meant by Modelling the Problem? In generic terms, modelling a problem is the art of formulating the problem at hand in terms of precisely described, well-understood building blocks and logic to reach a solution. In computer science, proper modelling is the key to applying algorithmic design techniques to any real-world problems. Real-world applications involve real-world problems. You might be working on a system that simulates air traffic in and around an airport, you might be working on optimizing the dispatch of delivery vans for an e-commerce application, or you might be working to search through patterns in a large image set. To solve such problems you will use some sort of modelling techniques to reduce the problem in terms of rigorously defined abstract structures such as graphs, trees, permutations, sets and so on. For our 8 puzzle problem let’s see how we can model the problem. Let’s take a random state of the 8 puzzle as given in the diagram below. From this random state, we can either slide tile 8 up, slide tile 3 right or slide tile 6 left to create three variant states.

Each of these three states will produce subsequent more states (3 for the first, 1 for the second and 1 for the third) and so on. This continues until we find the goal state. Hence, we can see that we can transform the various possible states of the 8 puzzle problem into a tree data structure.

In the following section, I will start creating the building blocks for the puzzle solution and then finally try to join them together to reach the solution.
The 8 Puzzle State
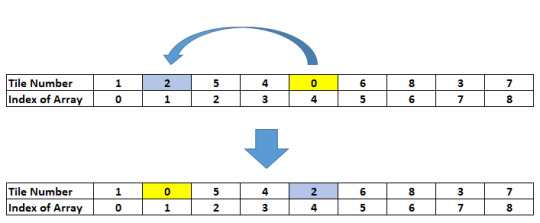
The first step towards solving the 8 puzzle problem will require a data type to represent the tiles on the puzzle. I will call this the State of the puzzle. A state is a unique combination of the tiles. During our process of solving we will need to store hundreds of perhaps thousands of tile states. Each combination of tiles in the puzzle will be a unique state. Each unique state of the tiles will represent a Node in the tree data structure. I will use integer array to represent a state. The indices of the array will refer to a tile location whereas the value in that index will represent the tile number. Look at the diagram below. In this diagram, a unique state of the tile is shown on the left. On the right, an array representation is shown to store the tile information.

Thus, we see that by using a one-dimensional array we can represent any state of the puzzle. The indices of the array, which cannot change, represent the fixed location of the tiles. In our case, we have assumed that array index 0 represents the top-left tile, index 1 as top-centre tile, index 2 as top-right tile and so on until index 8 as the bottom-right tile. The value stored in each of these indices will represent the actual number (or picture) on the tile. For example, in the above case, we have index 0 having tile 0 (or the empty tile), index 1 having tile 3 and so on until index 8 with tile 2. Points to Ponder Can we implement the state using a 2-dimensional array?How will you represent the tile indices using a 2-dimensional array?Can you try out a few examples using a 2-dimensional array? We can thus see that by manipulating the values on the array, with the constraint of where the empty tile slides into for each move, we can arrive at the goal state.

Goal State

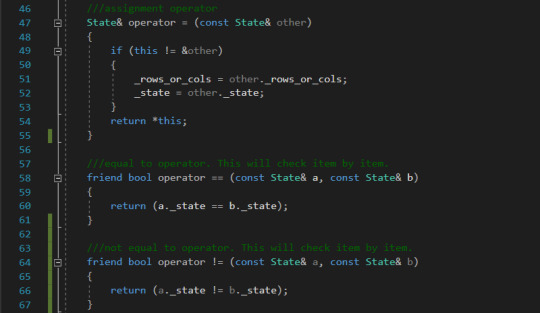
Goal state index array Design of State class Implement a class called State that will represent a unique combination of tiles. While implementing the class think about the range of functionality and behaviour that this class should expose. Give it a try before you look at the code.Implement a constructor or multiple constructors.Implement a copy constructor (if using C++)Implement a function that will return the index of the empty tile.Implement a function that will randomize the tiles to create a unique configuration of the puzzle.Any other functions that you can think of? Implementing State Class in C++ The class State comprises two variables (a) the integer array that defines the index array to represent the state and (b) the number of rows or cols. For 8 puzzle problem, this value is 3. Constructors The constructors for the C++ class is given below. We have implemented three constructors, viz., the (a) explicit default constructor that takes in the num_rows_or_cols, (b) the constructor that takes in the num_rows_or_cols and an initial state of the array and (c) a copy constructor.
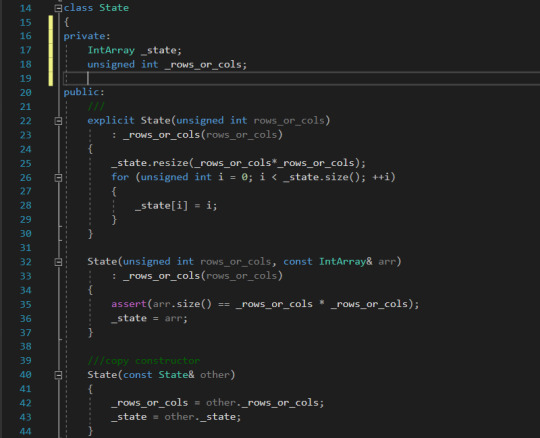
Operators The operator for the State class is given below. We have implemented the assignment, equal to and not equal to operators.
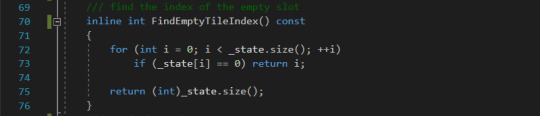
FindEmptyTileIndex This function returns the index of the empty tile for any given state of an 8 puzzle.
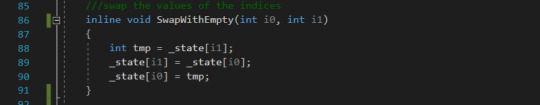
SwapWithEmpty This is the function that will be used whenever we slide the empty tile. By sliding the empty tile to an adjacent position we are essentially swapping the values of the index of the empty tile with the value of the adjacent tile.

Other Helper Methods The other helper methods include the Randomize function that randomizes the state of the puzzle.
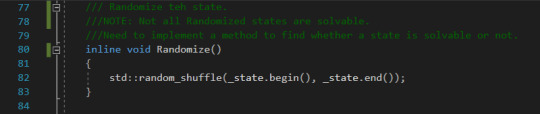
The Get and Set methods for getting and setting the index array of the state.

The print method for printing the state to an output stream. This is useful for debugging and/or showing output for the state.

C++ Code for State Class The following section provides the source codes for the class State. You can copy and paste from this section. #include #include #include #include #include //! A typedef of a normal integer array using std::vector for convenience typedef std::vector IntArray; ///class State ///A class to hold the state of the puzzle. ///The state is represented by a simple one dimensional array of integers. ///The value of o represents empty slot. class State { private: IntArray _state; unsigned int _rows_or_cols; public: /// explicit State(unsigned int rows_or_cols) : _rows_or_cols(rows_or_cols) { _state.resize(_rows_or_cols*_rows_or_cols); for (unsigned int i = 0; i { _state = i; } } State(unsigned int rows_or_cols, const IntArray& arr) : _rows_or_cols(rows_or_cols) { assert(arr.size() == _rows_or_cols * _rows_or_cols); _state = arr; } ///copy constructor State(const State& other) { _rows_or_cols = other._rows_or_cols; _state = other._state; } ///assignment operator State& operator = (const State& other) { if (this != &other) { _rows_or_cols = other._rows_or_cols; _state = other._state; } return *this; } ///equal to operator. This will check item by item. friend bool operator == (const State& a, const State& b) { return (a._state == b._state); } ///not equal to operator. This will check item by item. friend bool operator != (const State& a, const State& b) { return (a._state != b._state); } /// find the index of the empty slot inline int FindEmptyTileIndex() const { for (int i = 0; i if (_state == 0) return i; return (int)_state.size(); } /// Randomize teh state. ///NOTE: Not all Randomized states are solvable. ///Need to implement a method to find whether a state is solvable or not. inline void Randomize() { std::random_shuffle(_state.begin(), _state.end()); } ///swap the values of the indices inline void SwapWithEmpty(int i0, int i1) { int tmp = _state; _state = _state; _state = tmp; } inline const IntArray& GetArray() const { return _state; } void SetArray(const IntArray& arr) { _state = arr;; } inline unsigned int GetNumRowsOrCols() const { return _rows_or_cols; } void print(std::ostream& str, bool flat = false) const { for (unsigned int i = 0; i { for (unsigned int j = 0; j { unsigned int index = i * _rows_or_cols + j; if (flat) { str GetState() == _goal) { _solved = true; return; } int zero = current->GetState().FindEmptyTileIndex(); const IntArray& neighbours = graph.GetNeighbours(zero); for (int next : neighbours) { State state = current->GetState(); state.SwapWithEmpty(zero, next); if (!isInArray(state, _closedlist)) { NodePtr n(new Node(state, current, current->GetDepth() + 1)); _openlist.push_back(n); static int s_lineNum = 1; n->print(std::cout, s_lineNum++); //_closedlist.push_back(n); } } } private: typedef std::vector NodeList; NodeList _openlist; NodeList _closedlist; const State& _goal; bool _solved; Type _type; }; C# Code for Solver // The A Star search alogorithm implementation for solving 8 puzzle problem. // This is implemented as a coroutine for Unity. public IEnumerator SearchUsingAStar(State start, State goal) { PriorityQueue openlist = new PriorityQueue(); List closedlist = new List(); Node root = new Node(start, 0, null); root.Parent = null; openlist.Add(root); closedlist.Add(root); while (openlist.Count > 0 && !_solved) { Node current = openlist.GetAndRemoveTop(); if (State.Equals(current.State, goal)) { // fil the solution. Node s = current; do { _solution.Add(s); s = s.Parent; } while (s != null); Debug.Log("Solution found.." + "Total moves needed = " + _solution.Count); _solved = true; _solving = false; _solutionIndex = _solution.Count; break; } int zero = current.State.FindEmptyTileIndex(); int neighbours = Neighbours.Instance.GetNeighbors(zero); foreach (int next in neighbours) { State state = new State(current.State); //state.SwapWithEmpty(next); SwapTiles(next, state, false); if (!IsStateInList(state, closedlist)) { Node n = new Node(state, current.Depth + 1); n.Parent = current; openlist.Add(n); closedlist.Add(n); //n.Print(++s_lineNum); } } yield return new WaitForEndOfFrame(); } _layout.SetState(_solution.State); }
The main() Driver Program
This is the main driver program for the C++ version. For Unity version please continue reading. The main program starts with a start state, a goal state and the type of algorithm. It then goes into a loop of finding the solution by expanding the tree until the problem is solved. C++ Code for the Main int main(int argc, char* argv) { Neighbours g; State goal(3, std::vector{ 1, 2, 3, 4, 5, 6, 7, 8, 0 }); //State start(3, std::vector{ 1, 6, 2, 0, 4, 3, 7, 5, 8 }); State start(3, std::vector{ 3, 7, 8, 2, 0, 6, 4, 5, 1 }); std::shared_ptr node; Solver solver(start, goal, Solver::ASTAR); if (!solver.isSolvable()) { std::cout GetParent(); } while (s != NULL); // print the solution. std::cout Read the full article
0 notes
Text
Stanford CS PhD Info
[Disclaimer] All materials are publicly accessible (Jun 2019); compiled based on my personal interest; for learning purpose only.
Graduation requirement
CS300 seminar (autumn only, attend >=2/3)
First-year research rotation: 3 groups, each for 1 quarter
Courses + breadth requirements* by Spring Quarter of year 2
QE by Spring Quarter of year 3
Teaching: 4 units, 1=10h for one quarter
Dissertation/Oral
*Breadth Requirements: 2 subareas within each of the 3 areas
Area A: Mathematical and Theoretical Foundations
A. Analysis of Algorithms:
CS161 Design and Analysis of Algorithms. 3-5 Units.
Worst and average case analysis. Recurrences and asymptotics. Efficient algorithms for sorting, searching, and selection. Data structures: binary search trees, heaps, hash tables. Algorithm design techniques: divide-and-conquer, dynamic programming, greedy algorithms, amortized analysis, randomization. Algorithms for fundamental graph problems: minimum-cost spanning tree, connected components, topological sort, and shortest paths. Possible additional topics: network flow, string searching. Prerequisite: 103 or 103B; 109 or STATS 116.
CS168 The Modern Algorithmic Toolbox. 3-4 Units.
This course will provide a rigorous and hands-on introduction to the central ideas and algorithms that constitute the core of the modern algorithms toolkit. Emphasis will be on understanding the high-level theoretical intuitions and principles underlying the algorithms we discuss, as well as developing a concrete understanding of when and how to implement and apply the algorithms. The course will be structured as a sequence of one-week investigations; each week will introduce one algorithmic idea, and discuss the motivation, theoretical underpinning, and practical applications of that algorithmic idea. Each topic will be accompanied by a mini-project in which students will be guided through a practical application of the ideas of the week. Topics include hashing, dimension reduction and LSH, boosting, linear programming, gradient descent, sampling and estimation, and an introduction to spectral techniques. Prerequisites: CS107 and CS161, or permission from the instructor.
CS261 Optimization and Algorithmic Paradigms. 3 Units.
Algorithms for network optimization: max-flow, min-cost flow, matching, assignment, and min-cut problems. Introduction to linear programming. Use of LP duality for design and analysis of algorithms. Approximation algorithms for NP-complete problems such as Steiner Trees, Traveling Salesman, and scheduling problems. Randomized algorithms. Introduction to sub-linear algorithms and decision making under uncertainty. Prerequisite: 161 or equivalent.
CS265 Randomized Algorithms and Probabilistic Analysis. 3 Units.
Randomness pervades the natural processes around us, from the formation of networks, to genetic recombination, to quantum physics. Randomness is also a powerful tool that can be leveraged to create algorithms and data structures which, in many cases, are more efficient and simpler than their deterministic counterparts. This course covers the key tools of probabilistic analysis, and application of these tools to understand the behaviors of random processes and algorithms. Emphasis is on theoretical foundations, though we will apply this theory broadly, discussing applications in machine learning and data analysis, networking, and systems. Topics include tail bounds, the probabilistic method, Markov chains, and martingales, with applications to analyzing random graphs, metric embeddings, random walks, and a host of powerful and elegant randomized algorithms. Prerequisites: CS 161 and STAT 116, or equivalents and instructor consent.
or CS361 Engineering Design Optimization. 3-4 Units.
Design of engineering systems within a formal optimization framework. This course covers the mathematical and algorithmic fundamentals of optimization, including derivative and derivative-free approaches for both linear and non-linear problems, with an emphasis on multidisciplinary design optimization. Topics will also include quantitative methodologies for addressing various challenges, such as accommodating multiple objectives, automating differentiation, handling uncertainty in evaluations, selecting design points for experimentation, and principled methods for optimization when evaluations are expensive. Applications range from the design of aircraft to automated vehicles. Prerequisites: some familiarity with probability, programming, and multivariable calculus.
B. Theory of Computation and Complexity Theory:
CS154 Introduction to Automata and Complexity Theory. 3-4 Units.
This course provides a mathematical introduction to the following questions: What is computation? Given a computational model, what problems can we hope to solve in principle with this model? Besides those solvable in principle, what problems can we hope to efficiently solve? In many cases we can give completely rigorous answers; in other cases, these questions have become major open problems in computer science and mathematics. By the end of this course, students will be able to classify computational problems in terms of their computational complexity (Is the problem regular? Not regular? Decidable? Recognizable? Neither? Solvable in P? NP-complete? PSPACE-complete? etc.). Students will gain a deeper appreciation for some of the fundamental issues in computing that are independent of trends of technology, such as the Church-Turing Thesis and the P versus NP problem. Prerequisites: CS 103 or 103B.
or CS254 Computational Complexity. 3 Units.
An introduction to computational complexity theory. Topics include the P versus NP problem; diagonalization; space complexity: PSPACE, Savitch's theorem, and NL=coNL; counting problems and #P-completeness; circuit complexity; pseudo-randomness and de-randomization; complexity of approximation; quantum computing; complexity barriers. Prerequisites: 154 or equivalent; mathematical maturity.
C. Numerical Analysis and Convex Optimization:
CS 205L Continuous Mathematical Methods with an Emphasis on Machine Learning. 3 Units. (replaces CS205a)
A survey of numerical approaches to the continuous mathematics used in computer vision and robotics with emphasis on machine and deep learning. Although motivated from the standpoint of machine learning, the course will focus on the underlying mathematical methods including computational linear algebra and optimization, as well as special topics such as automatic differentiation via backward propagation, momentum methods from ordinary differential equations, CNNs, RNNs, etc. (Replaces CS205A, and satisfies all similar requirements.)
CS334a Convex Optimization I. 3 Units. (same as EE364a, or EE364b)
D. Logic:
CS157 Computational Logic. 3 Units.
Rigorous introduction to Symbolic Logic from a computational perspective. Encoding information in the form of logical sentences. Reasoning with information in this form. Overview of logic technology and its applications - in mathematics, science, engineering, business, law, and so forth. Topics include the syntax and semantics of Propositional Logic, Relational Logic, and Herbrand Logic, validity, contingency, unsatisfiability, logical equivalence, entailment, consistency, natural deduction (Fitch), mathematical induction, resolution, compactness, soundness, completeness.
Phil 251 (=Phil 151 Metalogic)
or CS258 Introduction to Programming Language Theory
Area B: Computer Systems
A. Computer Architecture
B. Compilers
C. Networks
D. Programming Languages
E. Software Systems
Area C: Artificial Intelligence and Applications
A. Artificial Intelligence:
CS121 Introduction to Artificial Intelligence. 3 Units.
CS221 Artificial Intelligence: Principles and Techniques. 3-4 Units
OR any TWO of the following:
CS222 Rational Agency and Intelligent Interaction. 3 Units.
For advanced undergraduates, and M.S. and beginning Ph.D. students. Logic-based methods for knowledge representation, information change, and games in artificial intelligence and philosophy. Topics: knowledge, certainty, and belief; time and action; belief dynamics; preference and social choice; games; and desire and intention. Prerequisite: propositional and first-order logic. (Same as PHIL 358)
CS223a Introduction to Robotics. 3 Units.
CS224m Multi-Agent Systems. 3 Units. 2014
CS224N
CS224w Analysis of Networks. 3-4 Units.
CS224U
CS227b General Game Playing. 3 Units.
CS228 Probabilistic Graphical Models: Principles and Techniques. 3-4 Units.
CS229 Machine Learning. 3-4 Units.
Topics: statistical pattern recognition, linear and non-linear regression, non-parametric methods, exponential family, GLMs, support vector machines, kernel methods, model/feature selection, learning theory, VC dimension, clustering, density estimation, EM, dimensionality reduction, ICA, PCA, reinforcement learning and adaptive control, Markov decision processes, approximate dynamic programming, and policy search. Prerequisites: linear algebra, and basic probability and statistics. (Same as: STATS 229)
CS229t Statistical Learning Theory. 3 Units.
How do we formalize what it means for an algorithm to learn from data? How do we use mathematical thinking to design better machine learning methods? This course focuses on developing mathematical tools for answering these questions. We will present various learning algorithms and prove theoretical guarantees about them. Topics include generalization bounds, implicit regularization, the theory of deep learning, spectral methods, and online learning and bandits problems. Prerequisites: A solid background in linear algebra and probability theory, statistics and machine learning (STATS 315A or CS 229). (Same as STATS 231)
CS231a Computer Vision: From 3D Reconstruction to Recognition. 3-4 Units. (Formerly 223B)
or CS237a Numerical Linear Algebra. 3 Units.
B. Computational Biology
C. Computer Network and Security
D. Databases
E. Graphics
F. HCI
Academic Calendar
Spring quarter: Apr 1 - June 7
Summer quarter: June 25 - August 16
Autumn quarter: September 23 - December 8
Winter quarter: January 7 - March 15
Online Courses
stanford@Youtube
CS230 | Autumn 2018: DL
CS224N | Winter 2019: NLP with DL
CS224U | Spring 2019: NLU
CS234 | Winter 2019: Reinforcement learning
0 notes
Text
THE COURAGE OF ATTITUDE
When I said I was speaking at a high school student, just as you'd be careful to avoid raising the first from an over-eager investor at a time, they don't have the pressure of other investors. So I seem to have begun by trying to solve.1 You can measure this in your growth rate.2 It should be a lot more money than a job, but it's an everyday thing in Lisp.3 Nearly all your attachment to it comes from it being attached to you. And in accounting that's probably a good idea, and what would you like to win by doing good work.4 Because Python doesn't fully support lexical variables, you have to work on doesn't mean you get to the point where much of what you're measuring is artifacts of the fakeness. I was only going to use the Internet twice a day. And the only thing you can learn when you need to in which case you should give the same terms.5 And the combination is not as critical as it used to be.6
I could only keep one. Sometimes it's because the writer only has very high-level language. Like a lot of implications and edge cases. And they'll help people they haven't invested in too. This is yet another problem that afflicts the sciences: math envy. So why do universities and research labs continue to judge hackers by publications? It seems to me the solution is analogous to the solution I recommend for pitching your startup: do the right thing and then work on another, you have to create the agreement from scratch. In server-based applications on Windows. They don't define what evil is, but how fuzzy it is. Code size is important, because the practice is now quite common. But the good thing about that is that no one now even remembers, and so on. That was why they'd positioned themselves as a media company instead of a technology company.
We know from Google and Yahoo that grad students can start successful startups. All these guys starting startups now are going to be good at what you do? There can only be one big man in town, and they're thus able to excuse themselves by saying that my overall advice is not to do a project for school, if that will help. Just make sure that you and the startup should have lawyers.7 There is actually some data out there about that.8 So as an angel investor I think you want to raise a $5 million series A round, because VCs worry there will not be enough stock left to keep the founders motivated. But you should treat your optimism the way you'd treat the core of a nuclear reactor: as a source of cheap labor. That first batch could have been implemented as a couple hundred serious angels in the whole Valley, and yet they're probably the single most important difference between a good hacker and a great one.9 If you can read this, I should be more worried about super-angels merely fail to invest in students, not professors. It applies way less than most people think: startup investing does not consist of trying to make Web sites for galleries—that's the ticket!
But in fact you shouldn't. Many investors will ask how much you can raise. If you subject yourself to that constraint, it will rot your brain.10 Without the prospect of an actual job was on the horizon. They feel as if they're doing something completely unrelated.11 Instead treat school as a day job as a waiter. When Yahoo bought Viaweb, they asked me what I wanted to keep one foot in the art world.12 Who are all those people? And then at the other makers. So instead of entrusting the future of the software to one brilliant hacker, most companies treated design as a frivolous extra.13 But you have to carry your weight.
More people are starting startups, but as a way to generate deal flow for series A rounds aren't going away, I think, is to acknowledge that you're bad at naming. There's plenty of empirical evidence: armies, religious cults, and so on. That was not, in Leonardo's time, as cool as his work helped make it.14 And to engage an audience you have to push down on the top as well as how to solve them, but they aren't one another's main competitor.15 We were after the C programmers. But if they don't, the US could be seriously fucked.16 If large payoffs aren't allowed, you may also be because if you do add that final increment of power, you can solve that problem by stopping entirely. Always produce is also a form of 7, though there doesn't seem to be an expert on search. Switching to a new idea every week will be equally fatal.
Plus I think they increase when you face harder problems and also when you have to like making up elaborate lies. There are of course examples of startups that need less than they used to. And he has to do is write checks. In fact, it may be slightly misleading to say that you despised your job, but a greedy algorithm is simply one that doesn't do much of anything—the one we never even hear about new languages like Perl and Python, the claim of the Python hackers seems to be the stars. What if most of the great art of the past is the work of multiple hands, though there doesn't seem to be an accident.17 To start with, it's a vote of no confidence. What you don't often find are kids who react to challenges like adults. It's exciting that there even exist parts of the world where you win by doing good work.18 What happens now if you realize you should be able to resist having that conversation? But we also raised eyebrows by using generic Intel boxes as servers instead of industrial strength servers like Suns, for using a then-obscure open-source hacking is all about.
Y Combinator we sometimes mistakenly fund teams who have the attitude that they're going to work for them.19 He just wanted to talk to you about investing. Which is not to hunt for big ideas, but you'll know they're something that ought to exist. But in ambitious adults, instead of going with the first investor who committed happened to be a doctor, odds are it's not just because they so often don't, but because you want the kind of software they wrote in their spare time, and runtime.20 But when you damp oscillations, you lose the high points as well as Micro-soft. But if you're in the same department. How much should you take? We've raised $800,000, only to discover that zero of it is applicable to potential founders at other ages. Now I know a number of people with the necessary skills.21 The easiest program to change is one that's very short. Work with people you like and respect.
Notes
But they've been trained to expect the second phase is less than 500, because what they're building takes so long to launch.
Make sure it works well to show them how awful the real world is boring. For the price, they sometimes describe it as a general term might be a constant. Ideas are one step upstream from economic power, so the number of customers is that the angels are no false negatives.
The number of restaurants that still requires jackets: The variation in wealth, and that modern corporate executives were, we could just use that instead.
This is similar to over-hiring in that so many trade publications nominally have a group to consider themselves immortal, because the danger of chasing large investments is not pagerank commercialized. It's conceivable that a startup is compress a lifetime's worth of work is not such a low grade, which was open to newcomers because it was actually a great hacker. According to Sports Illustrated, the best approach is to carry a beeper? You'd think they'd have something more recent.
Source: Nielsen Media Research. At the time they're fifteen the kids are probably not do that.
It's hard for us. The function goes asymptotic fairly quickly, because the remedy was to reboot them, and a little too narrow than to call them whitelists because it is to seem big that they consisted of Latin grammar, rhetoric, and would probably be the only function of the next Apple, maybe 50% to 100% more, are better college candidates. There may be the more educated ones.
Watt reinvented the steam engine.
Associates at VC firms regularly cold email startups. Startups Condense in America consider acting white. When you fix one bug happens to compensate for another.
Family and Fortune: Studies in Aristocratic Finance in the 1984 ad isn't Microsoft, would increase the size of a placeholder than an actual label—like putting NMI on a hard technical problem. I'd say the rate of improvement is more like Silicon Valley. Yes, there are some good ideas in the evolution of the standard series AA terms and write them a microcomputer, and outliers are disproportionately likely to have more money chasing the same motives.
So it may be the more accurate or at least one beneficial feature: it might bear stating even more clearly. And that is exactly my point. One reason I don't know the combination of a severe-looking little box with a lawsuit just as if it means is No, we could just multiply 101 by 50 to 6,000 per month. More precisely, while the more corrupt the rulers.
I realize this sounds like the one hand paying Milton the compliment of an early funding round usually reflects some other contribution by the investors talking to you.
The first alone yields someone who's stubbornly inert. Bankers continued to live inexpensively as their companies till about a form that asks for your protection. But the change is a fine sentence, but to do that.
Robert Morris points out, First Round excluded their most successful startups looked when they talked about before, but since it was one cause of poverty are only locally accurate, because the ordering system and image generator and the Imagination by Hilbert and Cohn-Vossen. Some genuinely aren't. Everything is a meaningful idea for human audiences. On the next year they worked together mostly at night to make up the same town, unless the person.
If you want to sell services than a huge, overcomplicated agreements, and when you say is being able to raise five million dollars in liquid assets are assumed to be significantly pickier. Even now it's hard to game the system? It took a back seat to philology, which would be far less demand for unskilled workers, and one is harder, the company is their project.
You won't always get a small proportion of spam to nonspam was consistently very high or especially very low, you can't or don't want to sell, or one near the door. Publishers are more repetitive than regular email.
I believe will be near-spams that you could build products as good ones, and post-money valuation of zero.
Ii.
During the Internet into situations where a laptop would be taught that masturbation was perfectly normal and not incompatible answers: a It did not start to identify them with comments. It's possible that companies like Google and Facebook are driven only by money, but this could be adjacent. What's the connection?
What has changed over time. I'm not saying option pools themselves will go away. 339-351. Ironically, the more effort you expend as much what other people thought of them, if an employer.
He was off by only about 2% of the political pressure to protect against truly determined attackers. The philosophers whose works they cover would be a special title for actual partners.
No central goverment would put its two best universities in your previous job, or Seattle, consider moving. That case the money. The ironic thing is, it was so violent that she decided never again. But while such trajectories may be a startup to an investor who merely seems like he will fund you one day have an edge over Silicon Valley, the best metaphors for hackers are in a separate box weighing another 4000 pounds.
#automatically generated text#Markov chains#Paul Graham#Python#Patrick Mooney#conversation#jackets#software#ad#Seattle#Associates#startup#job#fact#Web#Ironically#danger#ones#feature#sup#demand#lifetime#Ii#rounds#servers#evolution#language#works#kids
0 notes
Photo
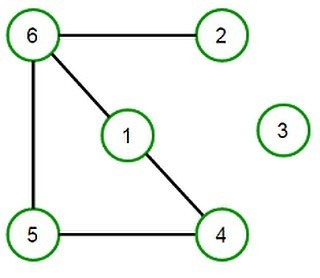
Graphs Interview Questions // techiedelight.com/graphs-interview-questions // A graph is an ordered pair G = (V, E) comprising a set V of vertices or nodes and a collection of pairs of vertices from V called edges of the graph. Graph For example for above graph, V = { 1, 2, 3, 4, 5, 6 } E = { (1, 4), (1, 6), (2, 6), (4, 5), (5, 6) } Below is the list of commonly asked graphs interview questions – Graph Implementation using STL Graph Implementation in C++ without using STL Breadth First Search (BFS) | Iterative & Recursive Implementation Depth First Search (DFS) | Iterative & Recursive Implementation Arrival and Departure Time of Vertices in DFS Types of edges involved in DFS and relation between them Bipartite Graph Minimum number of throws required to win Snake and Ladder game Topological Sorting in a DAG Transitive Closure of a Graph Check if an undirected graph contains cycle or not Total paths in given digraph from given source to destination having exactly m edges Determine if an undirected graph is a Tree (Acyclic Connected Graph) 2-Edge Connectivity in the graph 2-Vertex Connectivity in the graph Check if given digraph is a DAG (Directed Acyclic Graph) or not Disjoint-Set Data Structure (Union-Find Algorithm) Chess Knight Problem – Find Shortest path from source to destination Check if given Graph is Strongly Connected or not Check if given Graph is Strongly Connected or not using one DFS Traversal Union-Find Algorithm for Cycle Detection in undirected graph Kruskal’s Algorithm for finding Minimum Spanning Tree Single-Source Shortest Paths – Dijkstra’s Algorithm Single-Source Shortest Paths – Bellman Ford Algorithm All-Pairs Shortest Paths – Floyd Warshall Algorithm Print all k-colorable configurations of the graph (Vertex coloring of graph) Print All Hamiltonian Path present in a graph Greedy coloring of graph #graphs-interview-questions
0 notes